The purpose of this article is to provide information in the area of practical cryptography of interest to anyone wishing to use Encryption Software. This post covers starting from what is encryption, how encryption works, requirement for encryption and common usage of encryption in real world with examples.
What is Encryption?
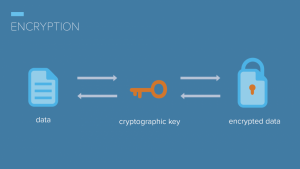
Encryption is the conversion of information into an cryptographic encoding that can’t be read without a key. Encrypted data looks meaningless and is extremely difficult for unauthorized parties to decrypt without the correct key.
Cryptography is the art or science of secret writing, or more exactly, of storing information (for a shorter or longer period of time) in a form which allows it to be revealed to those you wish to see it yet hides it from all others.
A cryptosystem is a method to accomplish this. Cryptanalysis is the practice of defeating such attempts to hide information. Cryptology includes both cryptography and cryptanalysis.
How Encryption Works?
The original information to be hidden is called “plaintext”. The hidden information is called “ciphertext”. Encryption is any procedure to convert plaintext into ciphertext. Decryption is any procedure to convert ciphertext into plaintext.
A cryptosystem is designed so that decryption can be accomplished only under certain conditions, which generally means only by persons in possession of both a decryption engine (these days, generally a computer program) and a particular piece of information, called the decryption key, which is supplied to the decryption engine in the process of decryption.
Plaintext is converted into ciphertext by means of an encryption engine (again, generally a computer program) whose operation is fixed and determinate (the encryption method) but which functions in practice in a way dependent on a piece of information (the encryption key) which has a major effect on the output of the encryption process.
A cryptosystem could be designed which made use of several different methods of encryption, the particular method chosen for a particular encryption process being key-dependent.
The combination of encryption methods results again in an encryption method, which is just as deterministic as a simpler cryptosystem, although probably harder for a cryptanalyst to crack.
A good cryptosystem should in fact vary the details of its encryption method in a key-dependent way, though high security does not require the combination of distinct encryption algorithms.
The result of using the decryption method and the decryption key to decrypt ciphertext produced by using the encryption method and the encryption key should always be the same as the original plaintext (except perhaps for some insignificant differences).
In this process the encryption key and the decryption key may or may not be the same. When they are the cryptosystem is called a “symmetric key” system; when they are not it is called an “asymmetric key” system.
The most widely-known instance of a symmetric cryptosystem is DES (the so-called “Data Encryption Standard”). The most widely-known instance of an asymmetric key cryptosystem is PGP (“Pretty Good Privacy”).
An encryption algorithm (a precise specification of the steps to be taken when encrypting plaintext and when decrypting the resulting ciphertext) is known as an “asymmetric algorithm” if the encryption and decryption keys that it uses are different; otherwise it is a “symmetric algorithm”.
Benefits for using Encryption:
There are many reasons for using encryption (examples are given below), and the cryptosystem that one should use is the one best suited for one’s particular purpose and which satisfies the requirements of security, reliability and ease-of-use.
- Ease-of-use is easy to understand.
- Reliability means that the cryptosystem, when used as its designer intended it to be used, will always reveal exactly the information hidden when it is needed (in other words, that the ciphertext will always be recoverable and the recovered data will be the same as to the original plaintext).
- Security means that the cryptosystem will in fact keep the information hidden from all but those persons intended to see it despite the attempts of others to crack the system.
When selecting an encryption, or cryptographic software, you should first consider what you want it to accomplish. There are numerous (entirely law-abiding) reasons why you might wish to conceal information, for example:
- Companies often possess data files on employees which are confidential, such as medical records, salary records, etc. Employees will feel safer knowing that these files are encrypted and are not accessible to casual inspection by data entry clerks (who may be bribed to obtain information on someone).
- Individuals may share working space with others, of whose honor they are not entirely sure, and may wish to make certain that in their absence no-one will find anything by snooping about in their hard disk.
- A company may wish to transfer sensitive business information between sites such as branch offices. Or it may wish to send confidential information (for example, a negotiating position, operating procedures or proprietary data) to an agent in the field (perhaps abroad). If the information is encrypted before transmission then one does not have to worry about it being intercepted since if this happens the encrypted data is incomprehensible (without the encryption key).
- A company may have information that a competitor would like to see, such as information concerning legal or financial problems, results of research, who the customers are and what they are buying, information revealing violations of government regulations, secret formulas or details of manufacturing processes, plans for future expansion or for the development of new products.
- A person or company may wish to transport to a distant location a computer which contains sensitive information without being concerned that if the computer is examined en route (e.g. by foreign customs agents) then the information will be revealed.
- Two individuals may wish to correspond by email on matters that they wish to keep private and be sure that no-one else is reading their mail.
From the above examples it can be seen that there are two general cases when encryption is needed:
- (a) When information, once encrypted, is simply to be stored on-site (and invulnerable to unauthorized access) until there is a need to access that information.
- (b) When information is to be transmitted somewhere and it is encrypted so that if it is intercepted before reaching its intended destination the interceptor will not find anything they can make sense of.
In case (b) there arises the problem of secure key exchange. This problem exists because the person who will decrypt the information is usually not the same as the person who encrypted the information.
Assuming that the decryptor is in possession of the decryption engine (normally a piece of software) how does the decryptor know which decryption key to use?
This information must be communicated to the decryptor in some way. If, during the course of this communication, the key is intercepted by a third party then that third party can intercept and decrypt the cipher text subsequently sent by the encryptor to the decryptor.
Common usage of encryption:
Filesystems
A filesystem such as a hard drive in a laptop may be encrypted such that a password is required to access data.
Devices
Devices such as mobile phones may be designed to use encrypted data storage by default.
Files
A single file can be encrypted. This can be done in addition to file system encryption. For example, a password management application will may encrypt its data with a master password.
Communication
Communication links such as a connection between a website and a browser are commonly encrypted using a standard known as SSL (Secure Sockets Layer).
Messages between a website and a browser may traverse vast physical distances and pass through many machines on the way. Encryption is intended to prevent anyone between the sender and receiver from accessing the data being sent.
Digital Certificates
Digital certificates are a means of confirming the identity of information services. An organization publishes its company name and a public key in a digital certificate issued by a certificate authority.
If you encrypt a message with that public key, only the organization listed in the certificate should be able to decrypt that message with its corresponding private key.
This is used to verify the identity of web sites by sending them a secret code encrypted with a public key from a certificate and testing if they are able to decrypt the message and send the secret code back to you.
Non-repudiation
Encryption based technologies such as digital certificates are commonly used to document proof that a transaction occurred and was authorized by a particular individual or company. This is known as non-repudiation.
For example, if a customer presents a smart card and a password when they purchase something it is difficult for them to claim they didn’t make the purchase.
Authentication
Encryption is widely used in authentication protocols to test the identity of a smart card, device or information service. This is typically based on public key cryptography whereby a secret is encrypted with a public key to confirm that an entity is in possession of the corresponding private key.
Conclusion
There are full of suspicious people on the Internet, and you need to protect
your identity and your most sensitive data from prying eyes.
That’s why we developed Encryption Softwares for Windows, macOS, Android and even USB sticks. With just one click or drag and drop, you can easily protect your most important data and become anonymous online.